Or, “Package Management in Practice for Debian/Ubuntu”
Keeping a Debian/Ubuntu system current isn’t glamourous—but it can make the difference between a stable, secure box and one you can’t trust. Here’s a tight, practical workflow with commands you’ll actually use.
👍Quick update workflow (daily/weekly)
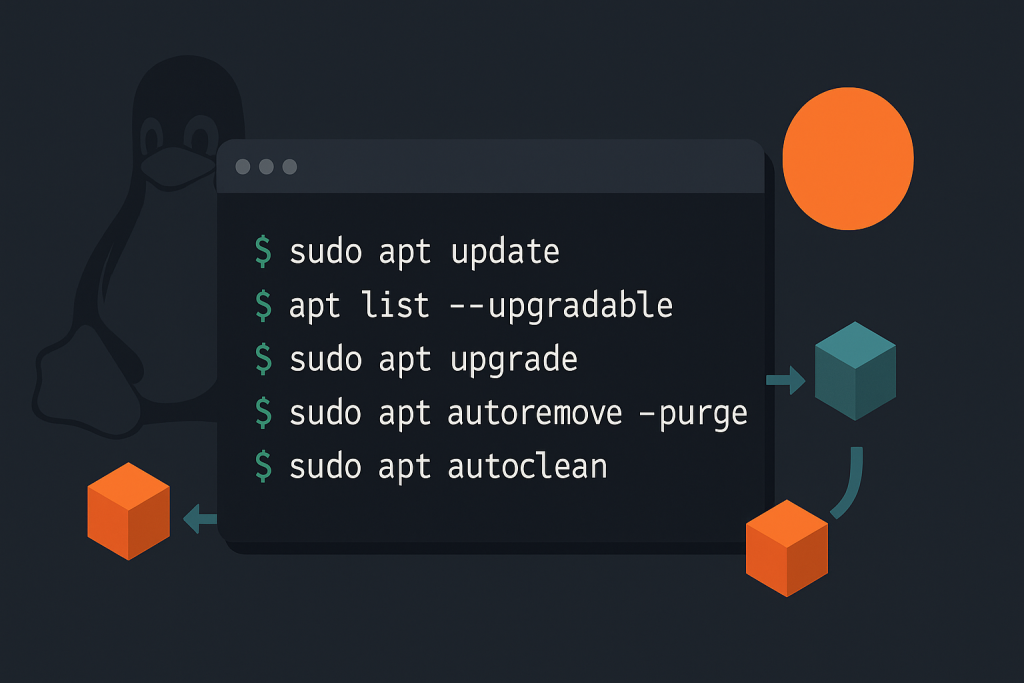
# 1) Refresh package indexes (what updates exist)
sudo apt update
# 2) See what would be upgraded
apt list --upgradable
# 3) Apply safe upgrades (no removals)
sudo apt upgrade
# 4) Remove leftover dependencies
sudo apt autoremove --purge
# 5) Clean downloaded package cache (optional)
sudo apt autoclean
# or wipe all cached packages:
# sudo apt clean🤔When Should I Reboot?
# If this file exists, a reboot is recommended (e.g., kernel/glibc):
test -f /var/run/reboot-required && cat /var/run/reboot-required || echo "No reboot required."🛠️Understand the Knobs that Matter
apt updaterefreshes the lists of available packages/versions.apt upgradeinstalls updates without removing packages.apt full-upgrademay add/remove packages to satisfy dependencies (use when major components change, e.g., kernel/graphics stacks).apt autoremove --purgegets rid of orphaned dependencies and their configs.apt (auto)cleantrims your local package cache (/var/cache/apt/archives).
TIP: Runupgradefor routine patching; usefull-upgradewhen you need to accept dependency changes.
🔒Security-first: Prioritize Security Updates
On most Debian/Ubuntu setups, security updates come from a …-security pocket. To check if pending updates are security-related:
apt list --upgradable | grep -i security
For Ubuntu, you can also enable automatic security patching:
# Install and configure unattended upgrades
sudo apt install -y unattended-upgrades
sudo dpkg-reconfigure --priority=low unattended-upgrades
# Verify the service/timer
systemctl status unattended-upgrades.service
sudo unattended-upgrades --dry-run --debugAuto-update cadence is controlled by files in /etc/apt/apt.conf.d/ (commonly 20auto-upgrades and 50unattended-upgrades). Typical minimal settings:
# /etc/apt/apt.conf.d/20auto-upgrades
APT::Periodic::Update-Package-Lists "1";
APT::Periodic::Unattended-Upgrade "1";🧸Hold back specific packages (when an update breaks your workflow)
Use holds sparingly and audit them regularly:
# Prevent a package from being upgraded
sudo apt-mark hold <package>
# Allow it to be upgraded again
sudo apt-mark unhold <package>
apt-mark showhold
✏️Verify what changed (and when)
# What got upgraded recently
less /var/log/apt/history.log
# Dpkg-level details (also check rotated logs: /var/log/dpkg.log.1, etc.)
grep " upgrade " /var/log/dpkg.log☑️Troubleshooting When Things Go Wrong (and they will)
# Broken/partial installs
sudo apt --fix-broken install
sudo dpkg --configure -a
# Lock contention (another package job running). Usually a background job (apt-daily.service) is active. Wait a minute and try again. Avoid manually deleting lock files; if a process is stuck, reboot cleanly.
systemctl status apt-daily.service apt-daily-upgrade.service
# Third-party repo problems. Check your sources, comment out any questionable entries, sudo apt update, and retry.
/etc/apt/sources.list
/etc/apt/sources.list.d/*.list🧰Minimal Monthly Maintenance (The 3Ms, or “Set it and Forget it”)
Reboot when /var/run/reboot-required appears (don’t procrastinate on kernel/glibc).
Run the quick workflow weekly.
Enable unattended-upgrades for security patches.
Review /var/log/apt/history.log monthly.
💪Follow the “Golden Path”
# Use this when you just want to patch and move on:
sudo apt update \
&& apt list --upgradable \
&& sudo apt -y upgrade \
&& sudo apt -y autoremove --purge \
&& sudo apt autoclean \
&& (test -f /var/run/reboot-required && echo "Reboot required." || echo "No reboot required.")That’s it—that’s all there is to a practical, predictable, and safe approach to keeping your Debian/Ubuntu systems updated!

Leave a Reply
You must be logged in to post a comment.