🔐 Introduction
Securing Linux servers isn’t just about keeping software patched—it’s about controlling how applications behave when attackers inevitably find a foothold.
AppArmor provides Mandatory Access Control (MAC) that locks down services with precise rules, ensuring they can only access the files, network, and resources they truly need for a job role or task.
In this case study, we walk through how Sarah, a sysadmin, hardened a vulnerable Ubuntu server by applying AppArmor profiles to Apache and a custom Python web app. The process highlights how simple configuration changes can stop real-world intrusion attempts without sacrificing performance.
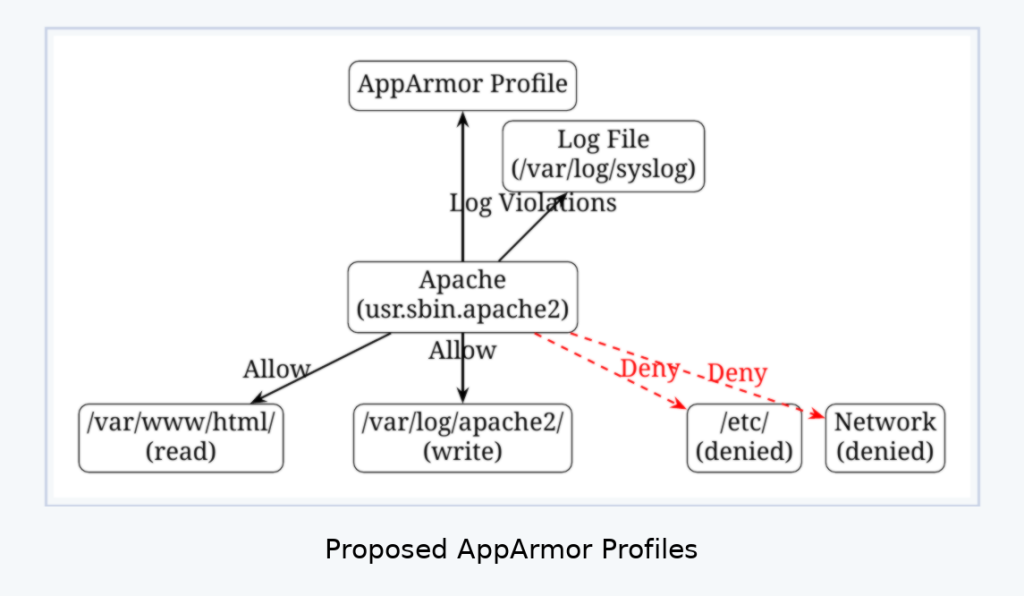
To help us visualize the restrictions Sarah has planned, the following diagram outlines her proposed AppArmor profiles. The diagram shows how Apache and the custom Python app will be confined to only the directories and resources needed, while sensitive areas like /etc and unnecessary network access will be denied. This demonstrates how AppArmor enforces a least-privilege model in practice:
🌀Scenario
- Server: Ubuntu 22.04 LTS, running Apache2 and a custom Python app (/usr/bin/webapp).
- Issue: Logs indicate attempts to access /etc/shadow and unauthorized network connections from the Python app.
- Goal: Use AppArmor to restrict Apache and the custom Python app, preventing unauthorized actions.
✅ Step-by-Step Hardening Process
- Verify AppArmor Installation
Sarah first checks if AppArmor is installed and active:sudo systemctl status apparmor.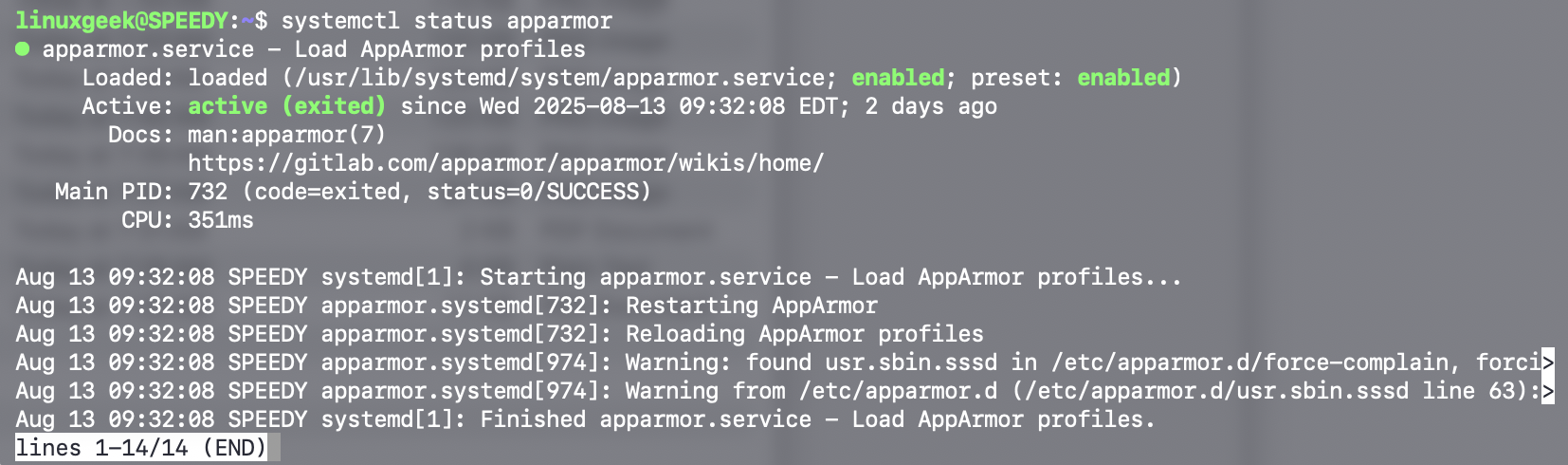
The terminal output confirms AppArmor is active and running. If not, you can install apparmor with:sudo apt install apparmor apparmor-utils - Enable AppArmor for Apache
Sarah enforces the default Apache profile:sudo aa-enforce /etc/apparmor.d/usr.sbin.apache2. This restricts Apache to accessing only/var/www/html/for reads and/var/log/apache2/for writes. Note: If Ubuntu complains that aa-enforce is not found, install the apparmor utilities packages withsudo apt update && sudo apt install apparmor-utils - Create a Profile for the Custom Python App
The custom app lacks a profile, so Sarah generates one:sudo aa-genprof /usr/bin/webapp. She then runs the app under normal conditions, allowingaa-genprofto log its behavior, then saves the profile to/etc/apparmor.d/usr.bin.webapp. - Restrict File Access
Next, Sarah edits the profile to allow only necessary file access:/var/webapp/data/** r, /var/log/webapp.log w, deny /etc/** r,to prevent the app from reading sensitive files like/etc/shadow. - Deny Network Access
The app doesn’t need network access, so Sarah adds:deny network,to block unauthorized connections detected in logs. - Test in Complain Mode
Sarah tests the profile in complain mode to ensure no legitimate actions are blocked:sudo aa-complain /etc/apparmor.d/usr.bin.webapp. She then monitors logs withsudo grep apparmor /var/log/syslogand adjusts the profile as needed. - Set to Enforce Mode
After testing, Sarah enforces the profile:sudo aa-enforce /etc/apparmor.d/usr.bin.webapp - Audit Logs
Next, Sarah sets up log monitoring to detect future violations:sudo grep apparmor /var/log/syslog. She notices blocked attempts to access/etc/shadow, confirming AppArmor’s effectiveness. - Integrate with Systemd
Sarah ensures the app’s systemd service applies the profile:sudo systemctl edit webapp.service # Add: AppArmorProfile=usr.bin.webapp - Backup Profiles
Finally, Sarah backs up profiles to avoid data loss:sudo cp -r /etc/apparmor.d /backup/apparmor.d
Summary
By methodically applying AppArmor, Sarah transformed a vulnerable Ubuntu server into a hardened system with strong access controls. Through default and custom profiles, she ensured Apache and the Python web app were confined to only the resources they required, while sensitive files and unnecessary network activity were denied.
Key outcomes included:
- 🚫 Improved Security: Unauthorized file access and network connections are blocked.
- 📊 Improved Visibility through detailed log auditing, supporting continuous hardening. Logs now provide actionable insights for further hardening.
- ⚡Improved Performance: No noticeable performance impact, as AppArmor is lightweight, adding protection without bloat.
This case study demonstrates that even modest configuration changes with AppArmor can significantly raise the security baseline of Linux servers. For sysadmins, adopting a least-privilege model through AppArmor isn’t just best practice—it’s a practical, lightweight defense against real-world threats.
💡 Take Action: Don’t wait for a security incident to expose weak points in your Linux environment! Test your profiles in complain mode, and begin confining your critical services today. Even small steps—like restricting file access or blocking unnecessary network activity—can drastically reduce your attack surface.
If this guide was helpful, share it with your team or community and encourage others to integrate AppArmor into their security workflow. Together, we can make Linux systems more resilient against real-world threats. 🚀

Leave a Reply
You must be logged in to post a comment.